The Social-Engineer Toolkit is an open-source penetration testing framework designed for social engineering. SET has a number of custom attack vectors that allow you to make a believable attack in a fraction of the time.
In this lab, you will be using SET to evaluate the different attacks that computer systems face.
The purpose of this activity is to provide information regarding how these programs function in order that adequate defenses can be designed and implemented. These programs should never be used in a malicious fashion against another user.
Part 1: Social Engineering Attacks
- Turn on the Windows VM. Open Turn Windows features on or off in the Start Menu or Control Panel. Enable Windows Process Activation Service.
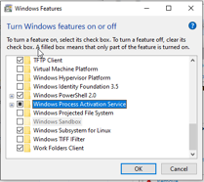
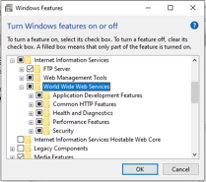
- Enable World Wide Web Services and its sub-services. Click OK then Close.
- Search for “Command Prompt” in the Start Menu and select Run as Administrator.
Restart the IIS manager.
iisreset /restart - Ensure that the Kali Linux VM is on a host-only network.
Turn it on and login.
Open the site for the Windows VM’s IP
http://192.168.56.101in a browser. It will be the Windows IIS homepage. - Search for in the Kali Linux start menu and launch the social engineering toolkit which is an open-source penetration testing framework designed for social engineering.
Enter the kali password when prompted.
Review and accept the terms with
y. You will see an error message for the tool failing to update, followed by the SET menu. - Enter
1to selectSocial-Engineering Attacks. Review the different types of attacks. - Enter
2to selectWebsite Attack Vectors. Review the different threat vectors. - Enter
3to selectCredential Harvester Attack Method. Review the different types of methods. - Enter
2to selectSite Cloner. Review the different types of tools. The tool is used to clone a webpage and harvest login credentials used on it for a simulated phishing attack. - When prompted for an IP address for the post back, enter the Kali Linux VM’s IP address
192.168.56.102. - When prompted for a URL to clone, enter the Windows IIS homepage
http://192.168.56.101. The tool is now hosting a site and waiting for connections to it. - In the Windows VM, browse to the Kali Linux IP at
http://192.168.56.102. The Linux server is pretending to be the Windows server. - In the Kali Linux VM, close all windows.
Open Terminal and see where the logs are kept.
sudo ls /root/.set/reports - Open the xml files.
sudo cat /root/.set/reports/*.xmlIf we were to clone a login page and login to the clone on the Windows side, this log file would contain the username and password used to login to the cloned site.
Part 2: Malware Attacks
- Open the main Social Engineering Toolkit menu and enter
4to selectCreate a Payload and Listener. Review the different threat vectors. - Enter
2to pickWindows Reverse_TCP Meterpreter. Review the various malware types. - When prompted for an IP address for the payload listener, enter the Kali Linux VM’s IP address
192.168.56.102. - When prompted for a port for the reverse listener, enter a random port
1111. - Once the SET tool creates the payload, enter
no. - Close all windows.
- Open Terminal again and view where the payload was placed.
sudo ls /root/.set - View the plaintext contents of the payload you’ve created.
sudo strings /root/.set/payload.exeIf we were to have entered
yesin step 18, it would begin to listen for an incoming connection, which would come if we were to run this payload on the Windows VM. That connection would create to a shell session from the Kali VM to the Windows VM with Metasploit’s framework. - Delete the payload.
sudo rm /root/.set/payload.exe - Uncheck the services enabled in steps 1 and 2. Shutdown all VMs.
- Please write up a paragraph answering the following questions.
- How could a user avoid logging into a social engineering site?
- How could a security administrator prevent the execution of payloads like these on their company’s systems?
- How could a penetration tester use a tool like this to help their company?