John the Ripper is a widely-used password cracking tool installed by default on Kali Linux. It supports various modes of password cracking including Single, Wordlist, and Incremental Mode.
The tool is developed by Openwall and is a free and open-source tool that is included in Kali Linux.
In this lab, you will be using John the Ripper to crack passwords on a Linux system.
The purpose of this activity is to provide information regarding how these programs function in order that adequate defenses can be designed and implemented. These programs should never be used in a malicious fashion against another user.
Part 1: Create a User
- Create a snapshot of the Kali VM. Turn on the Kali VM.
- In Terminal, create a user
clifford. You may have to enter your kali password if prompted.sudo useradd clifford
The sudo command gives you temporary superuser permissions to run the privileged action such as using the useradd command.
- Give the new account a password.
sudo passwd clifford - Enter
Reddogas the password. - Confirm that the account has been created.
id -u cliffordIt should return the user ID number.
- Repeat steps 2 and 3
to create another user
minniewithMickey!as the password. - Repeat steps 2 and 3 to create another user
studentwithpasswd1as the password. - Repeat steps 2 and 3 to create another user
gatsbywith1357as the password. - Repeat steps 2 and 3 to create another user
superuserwithkalias the password. - Repeat steps 2 and 3 to create another user
adminand this time choose a password that is 7 characters long.
Part 2: Crack Passwords
- Switch to the Desktop.
Then copy the passwd and shadow files from the /etc/ directory.
cd ~/Desktop sudo cp /etc/passwd passwd_copy sudo cp /etc/shadow shadow_copy
The passwd file stores usernames, user IDs, and password policies, while the shadow file stores their respective password hashes.
- Use the
pwdcommand to print your working directory, which should be/home/kali/Desktop.pwd - Enter
ls -lato view the files within your current directory. This will show you the read and write privileges, owners, sizes, last modified times, and names of the directory’s contents.ls -la
The top entry noted by . is essentially the working directory.
The second entry .. is essentially the containing directory.
In there, you’ll also see the two files you’ve just copied.
Notice the owner of those files.
Notice that all users have at least read permissions shown by r to the passwd_copy file, but only root has write permissions shown with w.
- Open each file to view its contents.
cat passwd_copy cat shadow_copy
Due to the file’s ownership, you may need superuser privileges to read the files.
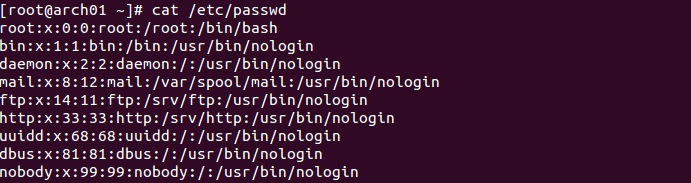
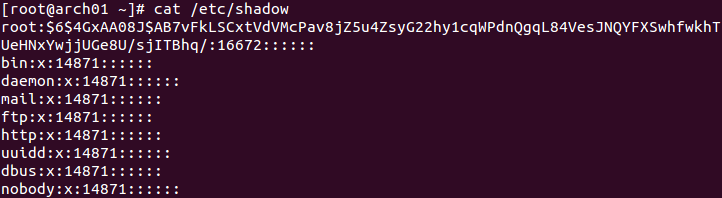
- Review the format of the passwd and shadow files. Notice that the password hashes are stored in the second column.
The passwords were at one time held in the /etc/passwd file, but it was since moved to the less permissive /etc/shadow file.
The /etc/passwd file now contains an x to indicate that the password is held in /etc/shadow, which would contain a hashed password for the user.
- Now, change ownership of the copied files to the kali user.
sudo chown kali ./*_copy - Repeat step 13 to confirm the new file owner.
- We’ll be using John the Ripper tools which are located in /usr/sbin/.
But if you use the
whichcommand as the kali user, notice that the system doesn’t recognize where thejohnexecutable is located as opposed to when it’s done withsudoprivileges.which john sudo which john - Print the environment variables and filter the output for “PATH”.
printenv | grep PATH - Look for the
PATHvariablePATH=/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/gameswhich is delimited by colons. Notice that /usr/sbin is missing.
Another way to view that environment variable is to echo it directly.
echo $PATH
- Add the directory to the
PATHvariable.export PATH=$PATH:/usr/sbin - Repeat step 18 to confirm that
johnis now found with the kali user. - Have John the Ripper’s unshadow tool merge the two files together.
unshadow passwd_copy shadow_copy > merged.txt - Purge any John the Ripper log files that may exist from previous runs.
Then begin cracking the passwords with the default wordlist.
rm /home/kali/.john/* john merged.txt
This may take a few minutes. If any remaining passwords are not cracked after 5 minutes, you may press Ctrl+C to stop it from continuing.
- Review the log files to see how long it took to crack each password and how long it took before the tool switched cracking modes.
grep 'Cracked\|Proceed' /home/kali/.john/john.log - Review the modes John the Ripper used by entering
john | grep modein the Terminal.john | grep mode
John the Ripper begins with simple checks to a dictionary comparison to more intensive brute-forcing. Single mode uses usernames to try to crack their passwords. Wordlist mode uses a dictionary file supplied by the user. Incremental mode uses brute-forcing to try to hash and compare every combination of characters, which could take a very long time.
- Read the comments in the John the Ripper wordlist.
Review to see if you can find some of the passwords in this wordlist.
grep comment /usr/share/john/password.lst - Turn off the Kali VM and restore it to the snapshot.
Write up a paragraph answering the following questions:
- In step 14, are the password hashes salted? How can you tell?
- Why did some passwords take longer than others to crack? What are the constraints on this tool’s performance?
- How could an administrator use what they know of John the Ripper to protect the user accounts on a system?