Cybersecurity is an exciting and rapidly growing field, and there are many opportunities for individuals who are interested in pursuing a career in this area. Entering the field of cybersecurity may seem daunting at first, but with a little preparation there are many pathways to getting started.
Whether you’re just starting out or looking to transition from another field, there are steps you can take to position yourself for success.
Why Cybersecurity?
Cybersecurity refers to the tools and techniques used to protect technology. Hardly a day goes by that we don’t hear about cybersecurity — whether it is a major breach of a corporate network or a mundane spam email, it bears risk.
It is a field that is incredibly exciting and ever-changing. The threats are refined just as quickly as the vulnerabilities are patched. Cybercrime is becoming more common and more expensive for organizations. This means more long-term opportunities for cybersecurity talent, which proves to be an intriguing career for many.
Unfilled Jobs
There are a half-million unfilled cybersecurity job postings in the United States. Cybersecurity professionals protect important and private information, from bank accounts to sensitive military communications. However, the shortage of skilled cybersecurity workers in the US poses a deep risk to our digital privacy and infrastructure.
Job Growth
There is an expected 33% job growth for cybersecurity careers compared to 7.7% for all occupations. This means that the cybersecurity skills gap will probably only get worse.
Salary
Cybersecurity jobs offer a 147% higher salary than average with many entry-level cybersecurity jobs starting at $45 an hour. The median salary for a cybersecurity analyst is $104K, much higher than the US average salary.
Variety of Roles
Cybersecurity offers a variety of positions across different industries, enabling candidates to find a role that aligns with their skills and experience. Before diving into how to get into a cybersecurity career, it is important to understand some of the 50 distinct cybersecurity roles to choose from.
Here are some of the most common roles in the field:
- Security Analyst : A security analyst is responsible for monitoring computer systems and networks for security breaches or intrusions. They analyze security risks and develop solutions to mitigate them.
- Penetration Tester : A penetration tester, also known as an ethical hacker, is responsible for testing computer systems and networks to identify vulnerabilities. They use tools and techniques to simulate attacks and identify weaknesses that could be exploited by malicious actors.
- Security Engineer : A security engineer designs and implements security systems to protect computer systems and networks from cyber attacks. They work closely with other IT professionals to identify vulnerabilities and develop effective solutions.
- IT Auditor : An IT auditor is responsible for evaluating the effectiveness of an organization’s information systems and controls. They conduct audits to ensure that the organization is compliant with relevant regulations and standards.
- Security Consultant : A security consultant provides advice and guidance to organizations on how to improve their security posture. They conduct risk assessments, develop security policies and procedures, and provide training to employees.
- Security Manager : A security manager is responsible for overseeing an organization’s security program. They develop and implement security policies and procedures, manage security staff, and ensure that the organization is compliant with relevant regulations and standards.
Cons
There are however considerable cons to working in cybersecurity.
Mental Burnout
It is very easy to mentally burn out since there is no time to relax, therefore this field requires serious passion and dedication.
Master of None
The learning never stops because the threats constantly change. Also, there is no true entry-level position since all levels have prerequisites.
Stay Curious
Many cybersecurity roles require a strong foundation in computer science, information technology, or a related field. There is never a time when you will feel like you know enough since there are always new technologies and tactics. Find ways to fill the gaps in your knowledge and experience. Search through existing cybersecurity job postings and take note of the technical skills they are seeking for the roles you are interested in. Spend some time familiarizing yourself and getting your hands on each technical skill.
Essential Technical Skills
Possessing the appropriate skills set can be crucial for securing a job in cybersecurity.
Operating Systems
Security threats exist across all operating systems. Become deeply familiar with MacOS, Windows, Linux, and their command-line interfaces.
Controls and Frameworks
In all cybersecurity jobs you will work on addressing gaps between an organization’s systems and the best practices. Learn the most common cybersecurity frameworks.
Incident Response
Quickly responding to security incidents is critical. Become familiar with incident response plans, network monitoring, digital forensics, and malware analysis.
Cloud
More businesses continue to move to cloud environments. Conduct projects with the three major cloud providers as well as DevOps tools.
Scripting
Automation is the future. Learn Python, SQL, and PowerShell.
Training
There are many ways to learn cybersecurity skills, including formal education, training programs, and online resources.
Formal Education
If you’re just starting out, consider pursuing a degree in a cybersecurity major. There are also many different majors that can lead to a career in cybersecurity, including computer science, information technology, and computer engineering. A degree in computer science can provide a solid foundation in programming, algorithms, and data structures. Alternatively, a degree in information technology can provide a broader introduction to topics in networking, databases, and systems administration.
While a degree is not required for many entry-level positions, many list a bachelor’s degree as a requirement. You may find it difficult to land a job without one.
Enrolling in a degree program can also qualify you for internships and other opportunities to gain hands-on experience in the field. Since entry-level positions require some experience, internships can be a great way to get your foot in the door.
Accredited Institutions
In addition to formal education, there are many training and certification programs that can help you develop the skills you need to succeed in cybersecurity. Look for programs that are accredited by industry organizations such as CompTIA, ISACA, ISC)², EC-Council, and SANS Institute. These programs can provide hands-on experience with the tools and technologies used in the field, as well as opportunities to network with industry professionals.
Online Resources
There are many great online resources you can use to develop your skills.
NetworkChuck, Professor Messer, and SimplyCyber offer free resources to learn cybersecurity, networking, and operating systems.
There are also many subscription-basededucational resources available through:
As with many fields, experience is key to landing your first cybersecurity job. Look for opportunities to gain experience in the field, such as internships, volunteer work, or entry-level positions. Many organizations offer internships or other opportunities for students or recent graduates, which can provide valuable networking contacts as well as hands-on experience.
If you’re not able to land a formal internship or position, consider working on personal projects to build your skills and experience. For example, you might try setting up a home lab to experiment with different security tools and techniques. Alternatively, you might join cybersecurity clubs or organizations to network with professionals in the field and gain insights into the latest trends and best practices.
Podcasts
Cybersecurity experts are turning to podcasts as a source of news and analysis. Many podcasts involve subject matter experts with lots of experience. Listening to podcasts is a great way to pick up terminology and current events.
Webinars
Webinars are a great way to learn about new technologies and trends in cybersecurity. Many webinars are free and can be accessed from anywhere. They are also a great way to network with other professionals in the field.
SANs regularly offers a free webinar series on a variety of topics.
Books
Books are a great way to learn about cybersecurity. Check out my book reviews for a list of recommended books.
Certifications
Certifications provide a great way to plan a career and learning roadmap. You can use them to prove your knowledge and skills to potential employers. Achieving one helps to distinguish you from similar candidates.
Studying for certifications, whether guided or self-paced, requires a time and money investment. Therefore, you should consider the return on investment (ROI) of a particular certification before deciding on pursuing it.
Choose a certification that is aligned to the role you want to land. Balance the cost of the certification with how in-demand it is, and thus determine if it is worth the investment.
Security Certifications
Cybersecurity certifications demonstrate your knowledge in protecting computer systems and networks from cyberattacks, which is essential in today’s increasingly digital world.
- CompTIA Security+
- Offered by CompTIA
- Covers security architecture, threats and vulnerabilities, and security operations
- EC-Council Certified Security Specialist (ECSS)
- Offered by the EC-Council
- Covers information security, network security, and computer forensics
- Systems Security Certified Practitioner (SSCP)
- Offered by (ISC)²
- Covers security operations and administration, access controls, risk identification, monitoring, and analysis
- GIAC Security Essentials (GSEC)
- Offered by the GIAC
- Covers security fundamentals, network security, and defense in depth
Offensive Security Certifications
Penetration testing certifications demonstrate your skills and knowledge in finding and exploiting vulnerabilities in computer systems and networks, which can help you protect organizations from cyberattacks.
- CompTIA PenTest+
- Offered by CompTIA
- Covers planning and scoping, vulnerability scanning, and attacks and exploits
- Kali Linux Certified Professional (KLCP)
- Offered by Offensive Security
- Covers Kali Linux administration, exploitation tools, and offensive scripting
- Mossé Cybersecurity Institute Certified Penetration Tester (MPT)
- Offered by the Mossé Cybersecurity Institute
- Covers information gathering, vulnerability assessments, and exploitation
- EC-Council Certified Ethical Hacker (CEH)
- Offered by the EC-Council
- Covers attack vectors, security tools and techniques, and security assessments
Cloud Certifications
Cloud certifications demonstrate your skills and knowledge in designing, deploying, and managing cloud-based infrastructure and applications, which can help you advance your career and earn a higher salary.
- AWS Certified Cloud Practitioner
- Offered by Amazon Web Services
- Covers cloud concepts, security and compliance, and AWS services
- Microsoft Certified: Azure Fundamentals
- Offered by Microsoft
- Covers cloud concepts, cloud governance, Azure services
- Google Cloud Certified: Associate Cloud Engineer
- Offered by Google
- Covers cloud infrastructure, management and security, and GCP services
- CompTIA Cloud+
- Offered by CompTIA
- Covers cloud architecture and design, security, and deployment
Systems Certifications
Systems certifications demonstrate your skills and knowledge in designing, implementing, and maintaining computer systems and networks, which can make you a more valuable asset to potential employers and help you earn a higher salary.
- CompTIA A+
- Offered by CompTIA
- Covers hardware, operating systems, networking, security, and troubleshooting
- CompTIA Linux+
- Offered by CompTIA
- Covers Linux system administration, security, scripting, and containers
- CompTIA Network+
- Offered by CompTIA
- Covers networking fundamentals, network implementations, and operations and security
- EC-Council Certified Network Defender (CND)
- Offered by the EC-Council
- Covers network defense fundamentals, security controls, and networking protocols
After achieving a certification, display it in many places including Credly, LinkedIn, and your résumé.
Connecting with Professionals
Do not underestimate the value of networking — it is often discounted, but an incredibly powerful skill. Building relationships with other security professionals helps to open more doors for you.
Reach out to:
- Security professionals in your field of focus
- Fellow students in the same boat as you
- Potential mentors or mentees
- Technical recruiters at companies you like
- Cybersecurity book authors and podcasters
Conferences
Conferences offer opportunities to network with security professionals and to get exposure to research There are countless cybersecurity conferences to choose from, including:
- Black Hat, Las Vegas, NV
- DEF CON, Las Vegas, NV
- The Diana Initiative, Las Vegas, NV
- RSA Conference, San Francisco, CA
- THOTCON, Chicago, IL
- Summercon, Brooklyn, NY
- CSAW, Brooklyn, NY
- BSides, local
There are many others, as well as smaller events hosted by meetups and cybersecurity associations. Consider volunteering at any of these events.
Use social media to create a professional brand. Use it to portray the personal story you want to show the public.
LinkedIn serves many purposes:
- Lists your work experience
- Shows your professional relationships
- Delivers useful posts about security issues
- Allows you to be noticed (if you are active)
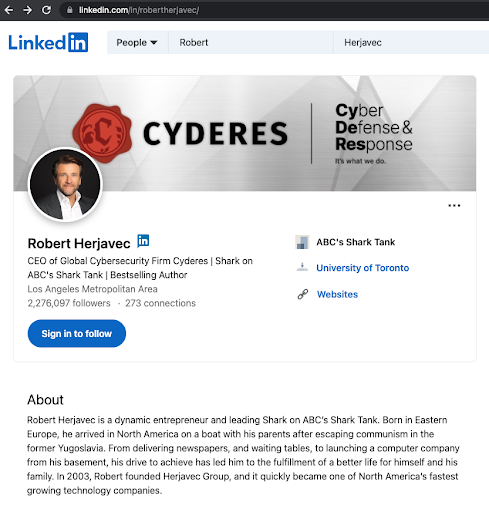
Look to the LinkedIn profile of a respected security professional for a baseline, in this case the profile of Robert Herjavec.
LinkedIn Profile: About
Upload a photo in professional attire. Customize your public profile URL. Add a summary in the About section to build your brand.
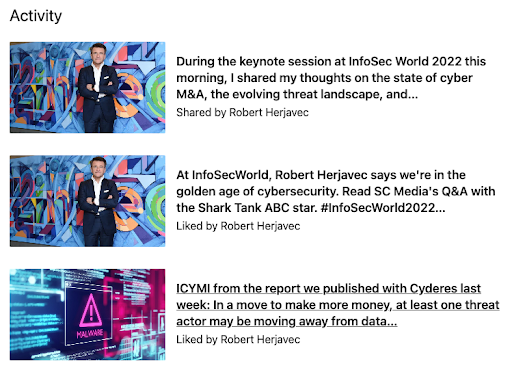
LinkedIn Profile: Activity
Be active on LinkedIn by commenting, liking, and posting your own content. Use hashtags when writing a post to have it reach the right audience. Many people will evaluate you by your feed, so keep it focused, courteous, and professional.
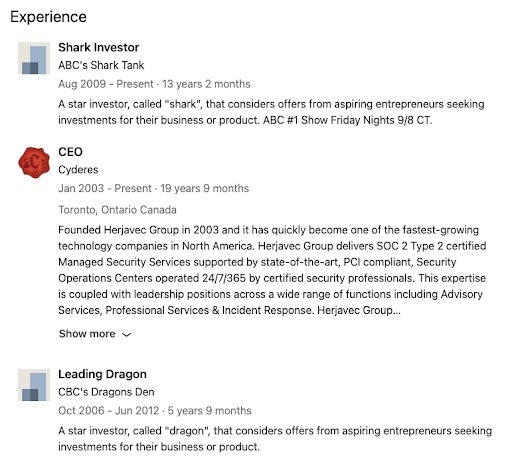
LinkedIn Profile: Experience
Use targeted keywords in your work history and include measurable results.
LinkedIn Profile: Other Sections
Include education you’ve received and programs you’ve attended. Enhance your profile by including relevant skills. Put in additional optional sections that add value.

GitHub
Your GitHub page provides a portfolio for recruiters to see your technical skills. Research what open-source security tools other professionals are using and contribute to those open-source projects. Consistently commit code to show your technical prowess and commitment.
References
Another benefit of networking is gaining references. It’s no longer necessary to include your references on your résumé, or at all. But, make sure you have at least three references (maybe teachers, mentors, colleagues, or former employers) who should be able to speak about your skills, experience, or character. Make sure to ask them ahead of time if they would be willing to serve as references.
The Ever-Changing Résumé
The résumé is your first impression, so it needs to be perfect and maintained regularly. Organizations receive hundreds of applications daily. The recruiter may spend only 7 seconds reviewing it, so make sure it is easy-to-understand and appealing.
- It should be no longer than 1 page for entry-level positions.
- Move the most important information to the top of the page since that is where the reader’s eyes will go first.
- Remove any irrelevant information since it will only distract the reader and therefore hurt your chances.
- Choose the experiences (including those with personal projects, volunteerism, training and education, and professional affiliations) that are related to the job.
- Be consistent with how and where you show dates, job titles, and other information.
Look to the résumé of a respected security professional for a baseline, but in this case we’ll use a generic one from Resume Worded.
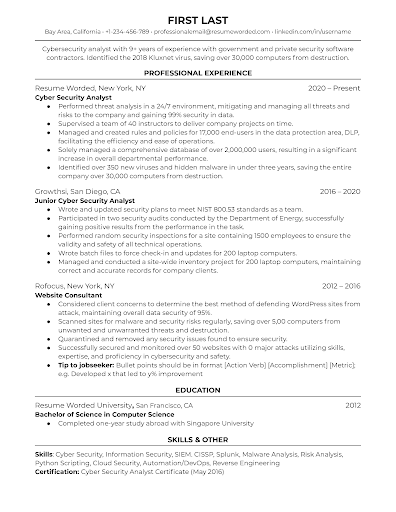
Résumé: Header and Summary
Include your phone number, an appropriately named email address, and a link to your LinkedIn or GitHub.
Do not include your full address, only the city and state.
Align your summary statement to the job that you are applying to. Explain to the reader why you are the best candidate for the position.
Résumé: Work Experience
Work experience is far more valuable than formal education, so it should be listed first if you have it. If you don’t, close the gap in a cover letter and in the interviews.
Take the perspective of a cybersecurity hiring manager since this is where they’ll likely spend the most time reviewing your résumé. Work history gives the hiring manager more context than job titles, so that is where they’ll spend their time.
Describe what you did in the role, the skills and tools you used, and how you helped the business. Format your bullet points with action, accomplishment, and metric. Quantify and qualify your achievements to show that you measurably improved the business.
- Implemented a new security awareness training program for 500 employees, reducing the number of phishing attacks by 50%.
Opt to use strong verbs like “led” and “designed” over soft verbs like “assisted” and “helped”.
Keywords
Résumés are typically passed through an Applicant Tracking System (ATS) where your résumé is compared to the job posting. Therefore, include keywords from the job description in your résumé if you have the experience.
Do not include keywords that you do not have experience with. It is unethical and you will be caught in the interview.
Ensure your résumé is keyword-optimized by checking it in a keyword visualizer.
Résumé: Education
Show that you continue to invest in yourself outside of formal education. Include bootcamps, self-learning, and conference attendance. Do not include a GPA unless you are a student, and only if it’s a great GPA.
Résumé: Skills and Certifications
List only skills for the type of job you are applying to. Be careful not to over- or under-sell yourself. If you are unsure, you could specify with “beginner”, “advanced”, and “expert” to set expectations.
Soft skills like communication, leadership, and teamwork are helpful but usually mentioned in the work experience. If it applies, specify if a certification is “in progress” or “expired”.
Also, include a section to show your professional extracurricular and volunteer activities.
The Interview Process
The interview process varies by company, by the level of the opening, and by how technical the role is. The order of the interview phases tends to be as follows.
Application
There are many free job search platforms online (Glassdoor, LinkedIn Jobs, Indeed, Google, ZipRecruiter, and CareerBuilder).
Cybersecurity job postings have a tendency to be imperfect and not accurately represent the job. Therefore, hiring managers do not expect you to know or have experience in everything listed — they may expect you to have two-thirds of the skills.
Research each organization for business health, trajectory, employee satisfaction, reputation, current events, culture, payscale, among other factors. Keep track of the jobs you are interested in and rank them based on the factors listed above. Choose the many that align with your goals and qualifications, and apply to them.
After a company receives your application, an automated Applicant Tracking System (ATS) filters your résumé. The system gives your résumé a match score and passes it on to the recruiter if there is a sufficient match.
Phone Screen
If you pass the application phase, the recruiter may reach out to you for a phone screen, which helps them determine if you are qualified for the role and are a good fit for their company. The questions are related to your work experience and the job description.
The phone screen lasts 15-30 minutes, so prepare with an interview notes form.
Tell me about yourself.
Practice your elevator pitch and keep it to 2 minutes. Match the job description to your experiences and ensure you bring up the top 3 essential ones.
What is your salary expectation?
Ahead of the phone screen, research the salary range for the position, which you can find on many sites including Glassdoor.
Do you have any questions for me?
Always have questions prepared for when they ask you this. Ask about the team, culture, and reporting structure.
If you never get to the phone screen phase, you should revise your résumé for future applications.
Technical Interview
In the technical interview phase, a member of the team tests your coding and technical abilities. This might be conducted over video call or as a take-home exercise. It may last about 1 hour. Depending on the job, you may be asked about your previous experience, specific technologies, or given a coding exercise.
For a coding exercise, ask questions before beginning your answer. They want you to anticipate issues and collect requirements before starting a project. If there are two possible answers, give the naïve solution then the better solution.
Coding exercises are stressful and time-sensitive, but it is important to remain communicative thorughout the interview. Ask for specific hints if you need them. Managers tend to prefer hiring a candidate who works well in teams than one with technical knowledge but only works alone.
To prepare for a coding exercise, practice on LeetCode.
Onsite Interview
In the final stage, your potential boss and colleagues assess you based on your past behavior. They will assess your soft skills in workplace situations.
Prepare by researching the company’s values. Keep a list of your previous experiences and projects as well as the situations you faced in each. Practice answering common behavioral interview questions to find areas for improvement in your responses.
In the interview, be specific and concise to hold their attention. Use real-life answers to show experience. Avoid using “we” and instead show how you contributed to something. Show that you are respectful and coachable. Avoid self-deprecation and never throw anyone under the bus, even if they deserve it. Always finish your answers on a positive note, perhaps with how you’ve learned from the experience you are talking about.
If you’ve made it this far, then the company is strongly considering hiring you.
STAR Method
The STAR method is one of the best ways to answer a behavioral interview question and expected for some top tech companies.
- Situation: Set the setting of the problem you faced
- Task: Explain your role in the situation
- Action: Explain the steps and reasoning you took to overcome the challenge
- Result: Summarize quantifiable impact of actions
For example, you may be asked:
Tell me about a mistake you made at work that you still remember today.
Think about why they would ask you this. Remember that the interviewer is a “customer” that needs to trust you and wants to see how you handle mistakes as well as what you learn from them.
You may want to respond in the STAR method format:
Back when I started my internship as a graphic designer, there was this time when I worked on the company’s annual report.
My manager asked for a small change after I had finished the work.
Since I had just reviewed everything, I made the change and checked only the page with that change before sending it back to her. I hadn’t noticed that something had broken the page numbers. My manager was very upset about receiving the work back with incorrect pagination.
Since then, I always double-check my entire work product, even after minor changes.
An Offer You Can’t Refuse
For good or bad news, the technical recruiter will (ideally) ask to speak with you. They may extend a tentative offer, which would show that you are their ideal candidate.
Recruiters are not your friends. They are salespeople who are trying to fill a position. They are not your advocate, so do not freely share your salary expectations with them without doing research first.
You typically want to negotiate the offer, especially if it falls below the range you asked for in the phone screen. Thank the recruiter for their consideration and ask if there’s room to negotiate the entry-level salary. Practice with colleagues or mentors if you feel awkward about negotiations.
If you never reach this point, continue to practice your interview and communication skills and keep trying.
Setting Up Goals
Consider the following questions:
What do you want to achieve in your career?
What skills do you want to develop?
What kind of work do you want to do?
What kind of company do you want to work for?
What kind of salary do you want to earn?
What kind of lifestyle do you want to have?
Now sit down and brainstorm your career goals. Don’t worry if they seem unattainable, which they might at first. You can always adjust them later. Draw a map of your career goals and how you plan to achieve them. Work backwards and list out the dependencies for a goal. What milestones would you need to achieve to get to that goal? Notice as you reach the initial task, how the goal becomes more and more realistic.
It takes hard work and dedication to land the first security job, so don’t limit your opportunities. As a last resort, consider pivoting into cybersecurity from an adjacent role such as IT support or systems administration and perform security tasks within that role. Use that experience to move into a security role later on.
When in doubt, refer to the “Cybersecurity Career Master Plan” and “Navigating the Cybersecurity Career Path”.




