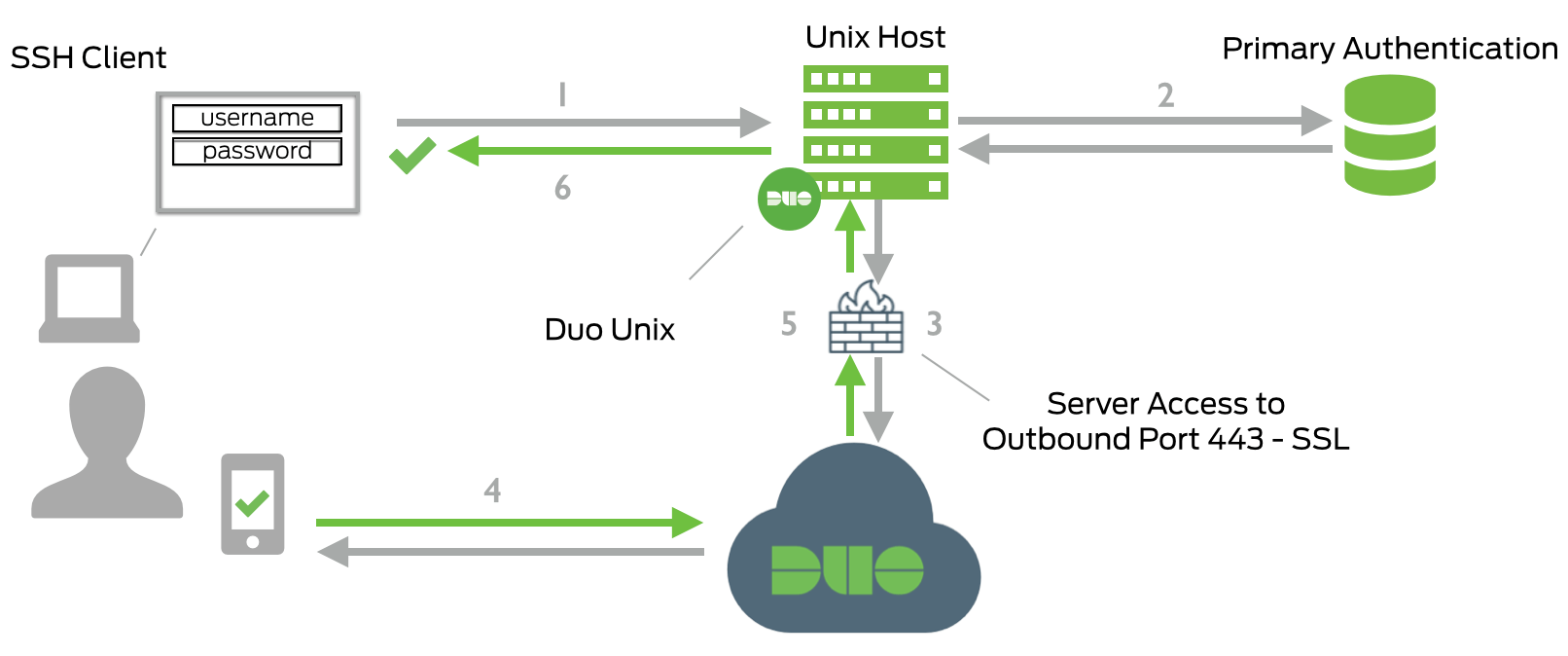
Duo MFA is a two-factor authentication solution that can be used to secure SSH logins. Using Duo MFA to secure SSH logins provides an additional layer of security beyond just a username and password.
With MFA enabled, even if an attacker manages to obtain a user’s password, they will still need to provide a second factor of authentication (such as a push notification to a mobile device) in order to gain access. This greatly reduces the risk of unauthorized access to the system, as it becomes much more difficult for attackers to bypass the authentication mechanisms in place.
In this activity, you will learn how to configure Duo Unix for SSH on Ubuntu.
Duo Unix Two-Factor Authentication for SSH
Duo Unix includes a command-line application called loginduo that allows users to perform two-factor authentication when logging in to their systems.
When a user attempts to log in, loginduo prompts them for their username and password, and then sends a push notification to their mobile device or phone. The user can then approve or deny the login request from their mobile device. If the user approves the request, they are logged in to the system. If they deny the request, the login attempt is rejected.
Part 1: Install Duo Unix on Ubuntu
These steps may vary depending on the Ubuntu operating system version.
- Add the Duo repository for the system’s package manager to download and install updates to the Duo Unix package.
ubuntu_version=$(lsb_release -c | awk '{print $2}') echo "deb [arch=amd64] https://pkg.duosecurity.com/Ubuntu ${ubuntu_version} main" | sudo tee /etc/apt/sources.list.d/duosecurity.list - Download and install the Duo Unix package on your system.
curl -s https://duo.com/DUO-GPG-PUBLIC-KEY.asc | sudo gpg --dearmor -o /etc/apt/trusted.gpg.d/duo.gpg sudo apt update && sudo apt install duo-unix
Part 2: Configure Duo Unix for SSH
-
Enable PAM authentication on your SSH server by editing the SSH daemon configuration file.
PAM (Pluggable Authentication Modules) is a framework for authentication that allows the use of multiple authentication schemes. It is used by many Linux distributions to provide a common interface for authentication. It is useful for integrating third-party authentication systems, such as Duo Unix.
echo "UsePAM yes" | sudo tee -a /etc/ssh/sshd_config - To use loginduo, configure your PAM stack to include the
authmodule provided by Duo Unix.echo "auth required pam_duo.so" | sudo tee -a /etc/pam.d/sshd -
Configure Duo Unix by adding your integration key, secret key, and API hostname to the configuration file.
You may find your Duo integration key, secret key, and API hostname by logging in to your Duo Admin Panel and navigating to Applications > SSH > New Integration.
Make sure to replace
INTEGRATION_KEY,SECRET_KEY, andAPI_HOSTNAMEwith your actual Duo integration key, secret key, and API hostname.sudo tee -a /etc/duo/login_duo.conf <<- EOF [duo] ; Duo integration key ikey = INTEGRATION_KEY ; Duo secret key skey = SECRET_KEY ; Duo API host host = API_HOSTNAME ; `failmode = safe` In the event of errors with this configuration file or connection to the Duo service ; this mode will allow login without 2FA. ; `failmode = secure` This mode will deny access in the above cases. Misconfigurations with this setting ; enabled may result in you being locked out of your system. failmode = safe ; Send command for Duo Push authentication pushinfo=yes autopush=yes EOFBe cautious if setting the
failmodeoption tosecure, as it may result in you being locked out of your system in the case of misconfigurations or connection issues with the Duo service.
- Test the configuration by attempting to log in to your SSH server. You should be prompted for your username and password, followed by a Duo two-factor authentication prompt.