AWS Automated Security Helper (ASH) is a tool that can be used to identify and remediate security vulnerabilities in code, infrastructure, and IAM configurations. By integrating ASH into your build pipeline, you can automate the process of identifying and remediating security vulnerabilities. This can help you improve the security of your software and reduce the risk of security breaches.
Once you have completed this lab, you will be able to integrate ASH into your own build pipeline and improve the security of your software.
Introduction to ASH
Part 1: Install ASH
- Follow the instructions in the Git lab to configure Git.
- In a terminal, navigate to the directory where you want to save the ASH tool.
Clone the ASH repository.
git clone git@github.com:aws-samples/automated-security-helper.git - Navigate to the ASH tool directory.
cd automated-security-helper - Temporarily set the ASH path in your shell environment.
This will allow you to run the ASH tool without having to install it.
export PATH=$PATH:$PWD
If you want to set the ASH path permanently, you will need to add it to your shell configuration file. For example, if you are using Bash, you can add the following line to your ~/.bashrc file:
echo "export PATH=$PATH:$PWD" >> ~/.bashrc
- Create a directory to store the ASH report.
mkdir ash-report export ASH_REPORT_DIR=$PWD/ash-report
Part 2: Scan Code for Security Vulnerabilities
Once the ASH tool has been installed, you can use it to scan your code for security vulnerabilities.
- Navigate to the directory that contains the code that you want to scan.
- Run the ASH tool.
ash --source-dir ./ --output-dir $ASH_REPORT_DIR
The --source-dir option specifies the directory that contains the code that you want to scan.
The --output-dir option specifies the directory where you want to save the ASH report.
The ASH tool will scan all the files in the specified directory and its subdirectories.
If you want to scan only certain files, you can use the --include option.
For example, if you want to scan only the files with the .js extension, you can use the following command:
ash --source-dir ./ --output-dir $ASH_REPORT_DIR --include *.js
- Once the ASH tool has finished scanning your code, you can review the ASH report to identify any security vulnerabilities.
Review the ASH report to identify any security vulnerabilities in your code.
cat $ASH_REPORT_DIR/ash-report.txtThe ASH report will contain a list of all the security vulnerabilities that were found in your code.
The following code sample shows an example of an ASH report:
Severity Vulnerability Location High Cross-site scripting (XSS) index.html:10 This example shows that an XSS vulnerability was found in the index.html file at line 10.
It is important to note that ASH is a static analysis tool. This means that it can only find security vulnerabilities that are present in your code. ASH cannot detect security vulnerabilities that are caused by runtime errors or other factors.
Static Code Analysis with ASH
In this lab, you will learn how to:
- Provision a CI pipeline leveraging AWS CodePipeline, AWS CodeCommit, and AWS CodeBuild
- Push a vulnerable Java application
- Integrate ASH in the pipeline
- Review results
- Fix the application
Part 1: Create a Repository
- In a browser, navigate to the AWS CodeCommit console.
- Choose Create repository.
- Enter a name and description for your repository.
- Choose Create to create the repository.
- Open the AWS CodePipeline console.
- Choose Create pipeline.
- Enter a name for your pipeline.
- Choose Next.
- In the Source section, choose AWS CodeCommit.
- In the AWS CodeCommit section, select the repository that you created in step 4.
- In the Branch name section, enter master.
- In the Change detection options section, select Amazon CloudWatch Events (recommended).
- In the AWS CodePipeline section, select Next.
- In the Build section, choose AWS CodeBuild.
- In the AWS CodeBuild section, select Create a new build project.
- In the Build project name section, enter a name for your build project (e.g. ASH-TestBuildProject).
- In the Environment section, select Managed image.
- In the Operating system section, select Ubuntu.
- In the Runtime(s) section, select Standard.
- In the Image section, select aws/codebuild/standard:5.0.
- In the Image version section, select Always use the latest image for this runtime version.
- In the Environment variables section, choose Add environment variable.
- In the Name section, enter AWS_DEFAULT_REGION.
- In the Value section, enter the AWS Region that you are using for this lab (e.g. us-east-1).
- In the Environment variables section, choose Add environment variable.
- In the Name section, enter AWS_ACCOUNT_ID.
- In the Value section, enter your AWS account ID.
- In the Service role section, select Create a service role in your account.
- In the Service role name section, enter a name for your service role (e.g. ASH-TestServiceRole).
- In the Additional configuration section, select Create build project.
Part 2: Configure the AWS CodeBuild Project
- Navigate to the AWS CodeBuild console.
- Select the build project that you created in step 15.
- Select Edit.
- Under Buildspec, select Use a buildspec file.
- In the Buildspec name section, enter buildspec.yml.
version: 0.2 phases: build: commands: - mvn clean package - ash --source-dir . --output-dir ./ash-report artifacts: - ash-report/This buildspec.yml file will install the ASH tool on the AWS CodeBuild project and run it on the source code. The ASH report will be saved in the ash-report/ directory.
- Select Save build project changes.
- Select Close.
- Select AWS CodePipeline.
- Select Edit.
- In the Build section, select AWS CodeBuild.
- In the AWS CodeBuild section, select the build project that you created in step 15.
Part 3: Configure the Deployment Stage
- In the Deploy section, select AWS CodeDeploy.
- In the AWS CodeDeploy section, select Create a new deployment group.
- In the Deployment group name section, enter a name for your deployment group (e.g. ASH-TestDeploymentGroup).
- In the Deployment type section, select In-place deployment.
- Configure the deployment to run on commit.
- In the Review section, select Create pipeline.
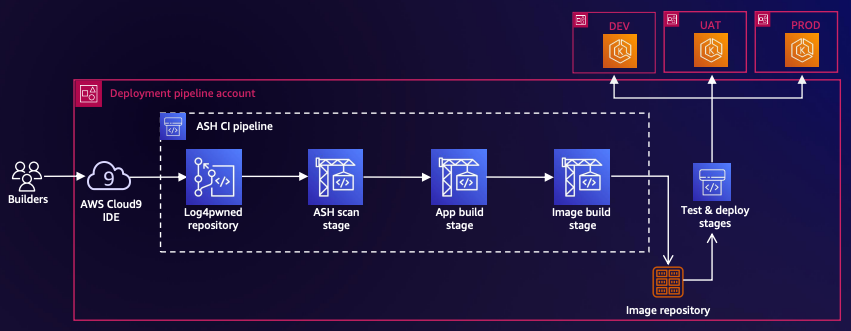
Part 4: Push the Code to the Repository
- Navigate to the AWS CodeCommit console.
- Select the repository that you created in step 4.
- Choose Branches.
- Choose Create branch.
- Add a vulnerability to the code.
To add a vulnerability to your code, you can add a malicious script to your code.
For example, the following code is a simple cross-site scripting (XSS) vulnerability:
<script>alert('This is a malicious script!')</script>
This is just a simple example of a Javascript vulnerability. There are many other types of vulnerabilities that ASH can detect in your code.
- Push the vulnerable code to the AWS CodeCommit repository.
To push the vulnerable code to your AWS CodeCommit repository, you can use the AWS CodeCommit CLI or the AWS CodeCommit console.
- Choose Commit.
- Choose Commit directly from the console.
- In the File field, enter the name of the file that contains the vulnerable code.
- In the Commit message field, enter a commit message.
- Choose Commit.
-
Choose Push. Once you have pushed the vulnerable code to your AWS CodeCommit repository, the AWS CodePipeline pipeline that you created in step 6 will automatically start running.
The ASH tool will scan your code for security vulnerabilities and generate a report in the ASHReport artifact.
Part 5: Reviewing Vulnerability Report
- Check the status of the AWS CodePipeline pipeline by opening the AWS CodePipeline console and selecting your pipeline.
- Once the pipeline has completed, you can review the ASH report to identify any security vulnerabilities in your code. The ASH report will contain a list of all the security vulnerabilities that were found in your code. It will be saved in the ASHReport artifact.
To review the ASH report, you can use a text editor or a web browser.
-
Review the ASH report to identify any security vulnerabilities in your code.
The following code sample shows an example of an ASH report:
Severity Vulnerability Location High Cross-site scripting (XSS) index.html:10 This example shows that an XSS vulnerability was found in the index.html file at line 10.
It is important to note that the ASH report is just a starting point. You should also review your code manually for security vulnerabilities.
Part 6: Fixing Vulnerabilities
If you find any security vulnerabilities in your code, you should fix them and push the fixed code to your AWS CodeCommit repository. The AWS CodePipeline pipeline will automatically start running again and the ASH report will be updated.
The specific steps to fix the security vulnerabilities in your code will vary depending on the types of vulnerabilities that were found. However, some general steps include:
- Removing any malicious code from your code.
- Sanitizing user input.
- Encoding user output.
- Using secure coding practices.
- To fix the XSS vulnerability from step 50, you can use the
escape()function to encode the special characters in the string.<script>alert(escape('This is a malicious script!'))</script>Encoding the special characters in the string will prevent the XSS vulnerability from being exploited.
- Push the fixed code to your AWS CodeCommit repository.
- Wait for the AWS CodePipeline pipeline to complete.
- Once the AWS CodePipeline pipeline has completed, review the ASH report to verify that the security vulnerabilities have been fixed and that there are no new security vulnerabilities in your code.
Severity Vulnerability Location This example shows that the XSS vulnerability was fixed and no longer exists in the code.