AWS Prowler is a free and open-source security tool that can be used to assess the security of AWS environments. It is a powerful tool that automates the auditing process against best practices and checks for any misconfigurations that could potentially lead to security breaches.
In this lab, you will learn how to install and configure Prowler in Docker and run it against your AWS environment.
Prowler can be installed in various ways, including as a Docker container, as a Python package, or as a standalone binary. In this lab, we will be using the Docker container.
Part 1: Install Prowler
To get started with Prowler, you will need to install it and configure it to access your AWS environment.
- In the terminal, create a folder named prowler-output/ to store the output of Prowler.
This folder will be mounted as a volume in the Prowler container.
mkdir prowler-output - Create a container named
prowlerbased on the official Prowler image from the Docker Hub.docker run -ti `# run in interactive mode` \ --rm `# remove the container after it exits` \ --name prowler `# name the container` \ --volume prowler-output:/home/prowler/output `# mount the prowler-output folder in the container` \ --env AWS_ACCESS_KEY_ID `# set the AWS access key ID` \ --env AWS_SECRET_ACCESS_KEY `# set the AWS secret access key` \ --env AWS_SESSION_TOKEN `# set the AWS session token` \ toniblyx/prowler:latest `# image name`
The --env AWS_ACCESS_KEY_ID, --env AWS_SECRET_ACCESS_KEY, and --env AWS_SESSION_TOKEN flags save your AWS credentials in cleartext in your bash history, Docker logs, and the Docker container.
This is a major security risk and should be avoided at all costs.
You can instead use the --env-file flag to set your AWS credentials from a file.
The credentials you use must have the following permissions:
- arn:aws:iam::aws:policy/SecurityAudit
- arn:aws:iam::aws:policy/job-function/ViewOnlyAccess
- prowler-additions-policy.json
- optional: prowler-security-hub.json
Part 2: Run Prowler
- The Prowler container should be running.
Review the available options by running the following command.
prowler --help
You can modify the configuration of Prowler by editing the prowler/config/config.yaml file.
- Review the available checks and AWS services by running the following commands.
prowler aws --list-checks prowler aws --list-services - Run the following command to run Prowler against your AWS environment.
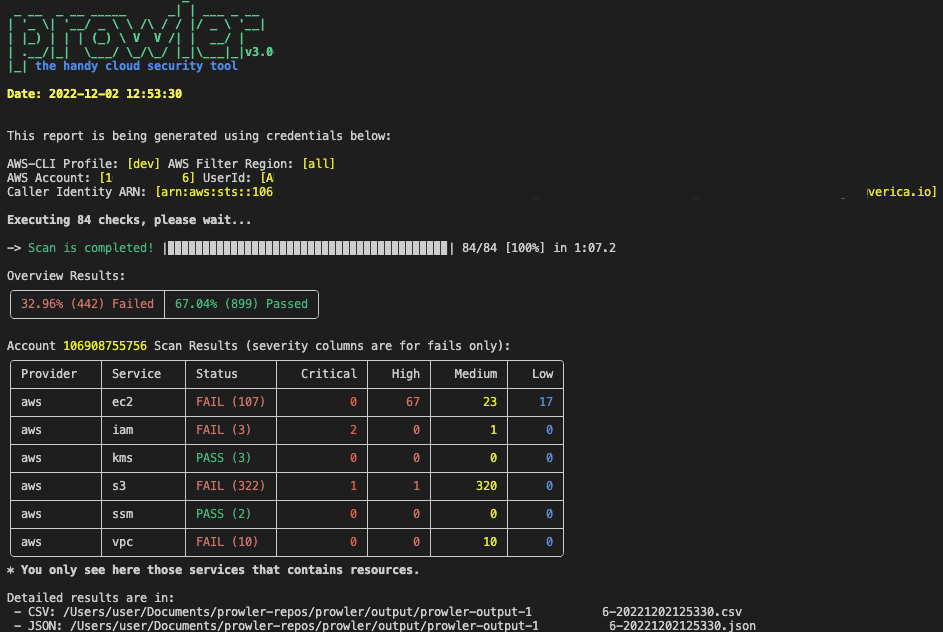
prowler aws
Prowler may take a long time to run, depending on the size of your AWS environment. Progress will be displayed as Prowler runs.
By default, prowler will scan all AWS regions.
To scan a specific region, use the --filter-region flag.
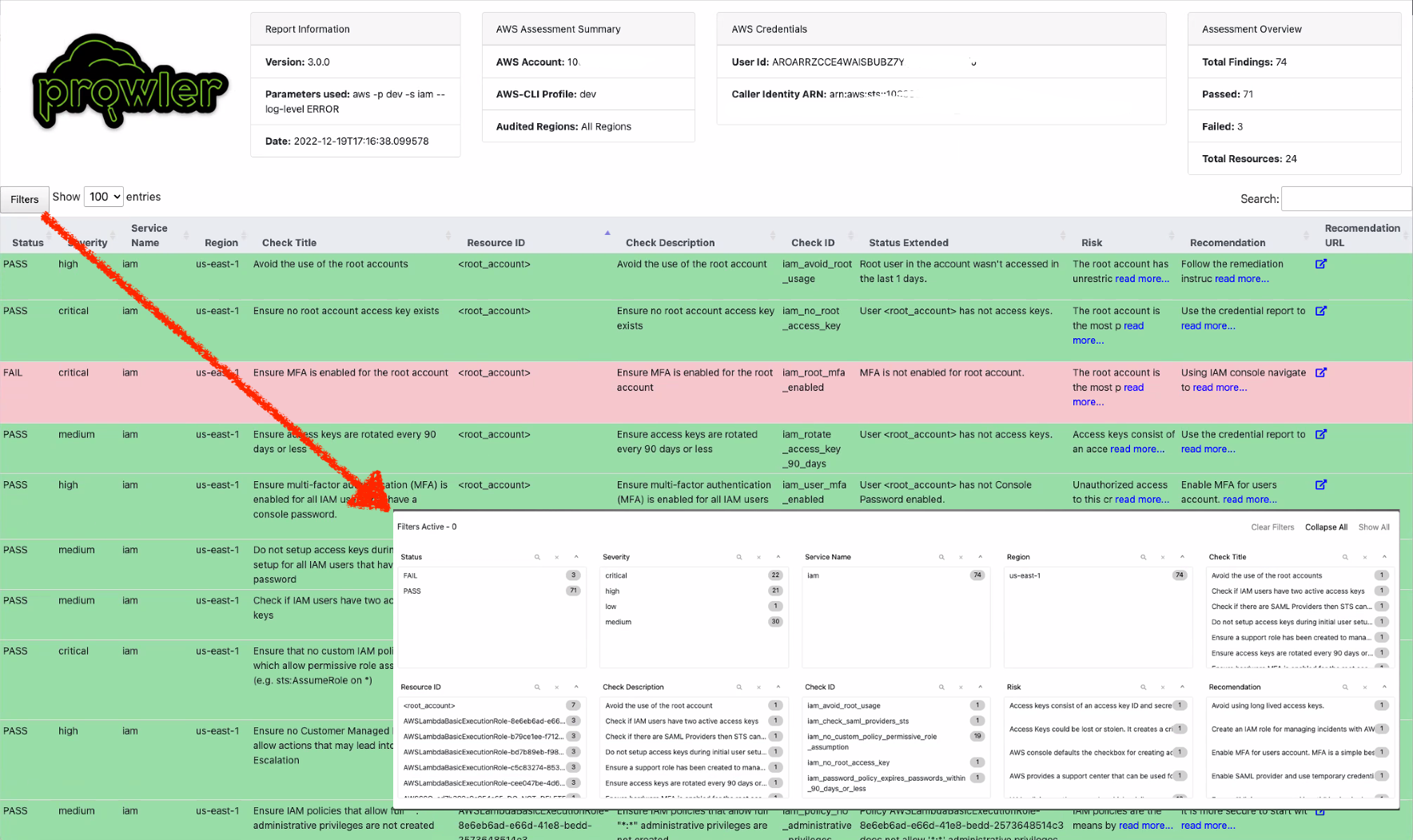
Part 3: Analyze the Prowler Results
- Once Prowler has finished running, you can stop the container by pressing Ctrl+C. This will stop the container and remove it.
- Review the output of Prowler in the prowler-output/ folder.
ls prowler-output -
Open the results to identify any misconfigurations or compliance violations. The report will provide a detailed overview of any security misconfigurations that were found, along with recommendations on how to address them.
open prowler-output/prowler-report.html
The open command is only available on macOS.
The results are also available in JSON and CSV format in the prowler-output/ folder.